Our Senior Solutions Architect Anthony Owen, explains the various types of ransomware and how they infiltrate your IT systems and network. But more importantly, what you can do to secure and respond to threats, turning those bad days caused by cyber threats, into More Good Days.
In today's interconnected world, cyber threats are ever-evolving, with ransomware posing a significant risk to users and organisations of all sizes. Ransomware is a malicious software, that encrypts![]() files or restricts access to computer systems, demanding a ransom payment in exchange for restoring normal operations.
files or restricts access to computer systems, demanding a ransom payment in exchange for restoring normal operations.
Understanding the differences between these is crucial for developing effective security strategies to prepare, protect and respond to these cyber threats.
Types of ransomware
Crypto Ransomware
Crypto ransomware is the most prevalent type of ransomware. It operates by encrypting files on the victim's computer or network, rendering them inaccessible. The attackers then demand a ransom payment, typically in cryptocurrency, in exchange for providing the decryption key to restore the files. Crypto ransomware spreads through various channels, such as malicious email attachments, compromised websites, or exploit kits targeting vulnerabilities in software.
Locker Ransomware
Locker ransomware takes a slightly different approach than crypto ransomware. Instead of encrypting files, it locks users out of their computer or device, preventing access to the system's resources. Once the device is infected, the victim encounters a full-screen message displaying the ransom demand and instructions to make the payment. Locker ransomware is again, often distributed through deceptive emails, disguised as legitimate notifications or downloads, fooling users into activating the malware.
Scareware
Scareware employs psychological tactics to deceive and intimidate victims. It masquerades as legitimate security software or displays false warning messages, tricking users into believing their system is infected with malware or viruses. Scareware typically prompts victims to take immediate action by paying a ransom to remove the supposed threats or to purchase a fake antivirus program. It preys on fear and urgency, exploiting users' lack of knowledge or fear of losing data.
Leakware
Also known as Doxware, Leakware represents a particularly insidious variant of ransomware. Instead of encrypting or locking files, it focuses on extracting and threatening to release sensitive or confidential information unless a ransom is paid. Cyber criminals often gain access to personal data through phishing attacks or by exploiting vulnerabilities in software. Once in possession of the victim's sensitive information, the attackers issue threats of exposure or sell the data on illicit marketplaces.
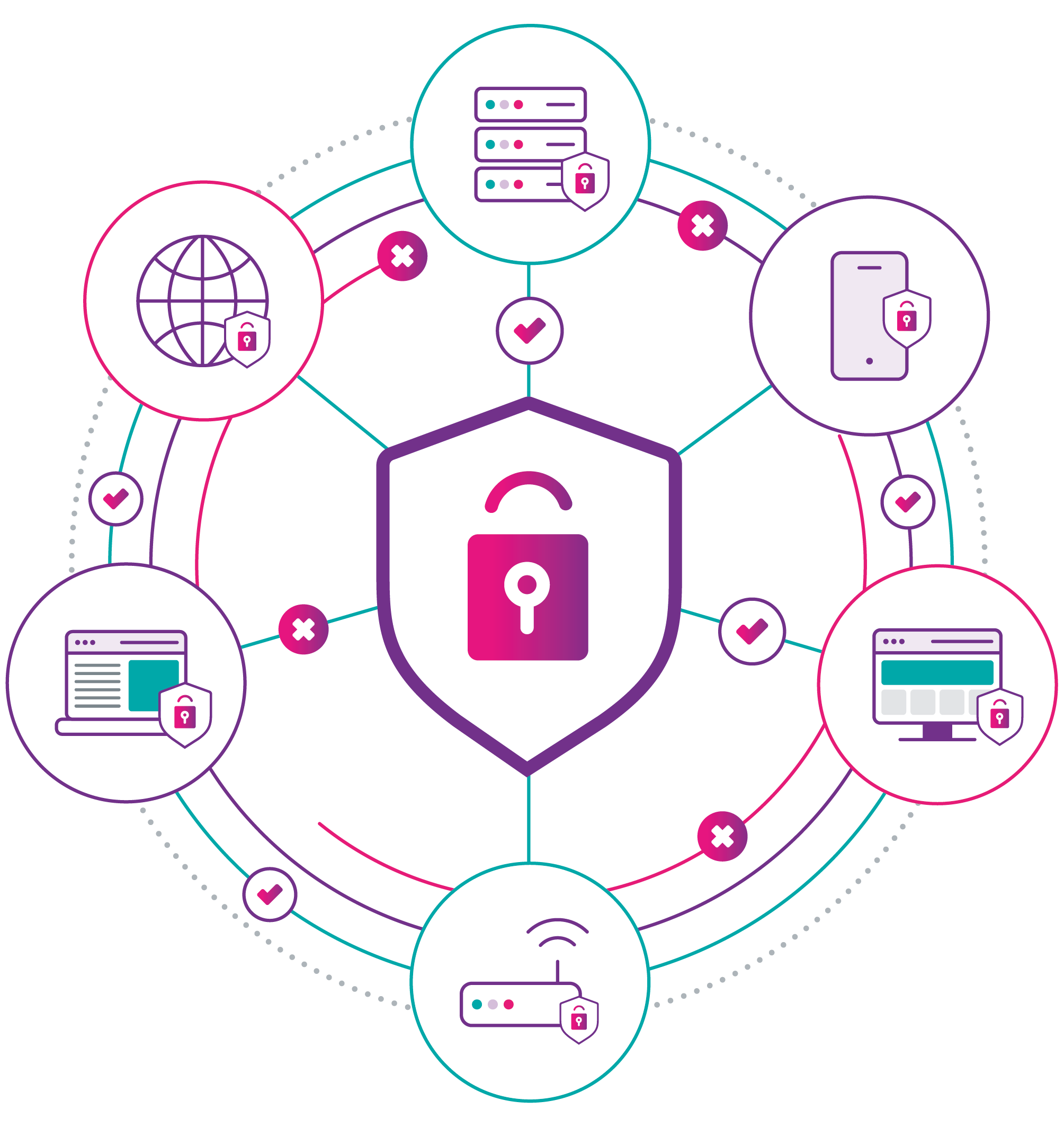
Protecting against cyber threats
To combat these different types of potential malware, it is important to adopt a defence-in-depth approach to security. The first line of defence against malware would be to block access to the destinations that host threats, so users cannot access these sites and download the malicious content. To achieve this, a secure web gateway solution such as Cisco Umbrella should be implemented.
Cisco Umbrella
Cisco Umbrella leverages DNS (Domain Name System) and IP filtering to block access to known malicious domains and IP addresses. When a user attempts to access a website, Umbrella checks the DNS request against a comprehensive and constantly updated database of malicious domains. If a match is found, Umbrella blocks the connection, preventing the user from accessing the malicious site and minimising the risk of malware infection.![]()
Umbrella also acts as a secure web proxy, intercepting web requests made by users and inspecting the traffic for potential threats. The solution analyses web content, including downloads and file transfers, in real-time to detect and block malicious files or URLs associated with malware distribution. By scanning web traffic, Umbrella prevents users from inadvertently downloading malware from compromised or malicious websites.
To get started with Umbrella, we are currently offering a FREE Cisco Umbrella trial, book your demo here.
Cisco Secure Firewall
The next layer of protection against malware would be at the network perimeter, which should be protected by Next Generation Firewall (NGFW) capabilities. An example of this would be the Cisco Secure Firewall or Meraki MX solutions.
Cisco NGFW devices incorporate an Intrusion Prevention System (IPS) that uses advanced threat intelligence and signature-based detection to identify, and block known malware signatures. It actively monitors network traffic and compares it against a vast database of known malware signatures to detect and prevent malicious activities in real-time. By leveraging IPS, NGFWs can proactively identify and block malware before it enters the network.
NGFWs incorporate Cisco's Advanced Malware Protection technology, which employs multiple techniques to detect and mitigate both known and unknown malware. It utilises signature-based detection, behaviour-based analysis, sandboxing, and machine learning algorithms to identify and block malicious files and processes. This multi-layered approach helps to detect and stop sophisticated malware threats that may evade traditional security measures.
Cisco Secure Endpoint
Finally we have the last line of defence., the Endpoint Detection & Response (EDR) solution. Most commonly seen solutions include Cisco Secure endpoint and Microsoft Defender for Endpoint.
![]() EDR Solutions employ advanced malware detection techniques to identify and prevent malware infections. It uses a combination of signature-based detection, behavioural analysis, machine learning, and heuristics to identify known and unknown malware threats. By continuously monitoring endpoint activity and file behaviour, EDR solutions can detect and block malicious files or processes attempting to infiltrate the system.
EDR Solutions employ advanced malware detection techniques to identify and prevent malware infections. It uses a combination of signature-based detection, behavioural analysis, machine learning, and heuristics to identify known and unknown malware threats. By continuously monitoring endpoint activity and file behaviour, EDR solutions can detect and block malicious files or processes attempting to infiltrate the system.
To learn more about Cisco Secure Endpoint and book your FREE trial today.
It is important to remember that the types of solutions listed above should be considered as the starting point for an overall security architecture that can protect you against Ransomware. There is however, an additional element that can bring huge benefit!
Piecing together the jigsaw puzzle for More Good Days
Imagine a security event as a large jigsaw puzzle. Each individual component in your security architecture can provide you with a handful of “jigsaw pieces”. When viewed in isolation, they give you a very small piece of the picture, and it is easy to misinterpret or lack the visibility needed of the wider scene and fully understand the wider context of what may be happening during a security event.
An eXtended Detection & Response (XDR) platform can be implemented to pull all the jigsaw pieces together. An XDR solution is designed to collate event information from the different security solutions, apply machine learning and artificial intelligence to help prioritise response to an incident. It will tell you where to act first, and the actions that should be taken.
Download our report
The last two years have forced organisations to rethink the way we work, with more and more organisations adopting remote and hybrid working models as part of their long-term strategy. When the security challenges and threat landscape changes as much as the technology, how can you be sure you’ve got a joined up approach, and are protecting your organisation and users in the smartest and most effective way possible?
Our survey’s findings point to a time of transition in IT circles, as employees seek smarter, more automated security tools to relieve them of more monotonous tasks – and to open up the more proactive and strategic aspects of their roles. The challenge is being set, and at CAE we’re blazing a trail from the mundane to the marvellous with smarter, intelligent technology that transforms user experiences – and helps deliver more good days at work.